The need for network security only increases with time. As the Internet of Things becomes mainstream, new challenges are added to what was already a complex subject. It is necessary to understand potential issues for security on both the physical and application sides. A security plan must address not only unauthorized access to a network, but also actions that could degrade performance or disable a network entirely, such as a maliciously inducted broadcast storm.
An effective security policy should provide strong protection from all vectors, and can be broken into four phases: assessment and deployment, detection, recovery, and remediation.
Phase 1 – Assess security and performance needs and deploy equipment
The first step is to identify and rank possible issues and risks. This includes not only analyzing the physical infrastructure, but also the processes and company policies through which humans interact with that infrastructure. Assessment should also consider the asset value of information assets. Typically, high value assets are located in the core side of a network, while assets of medium and low value are in the collection and access layers, respectively. Risks such as unused backbone connections and unattended equipment rooms are examples of risks to assets with high value.
Physical protection measures include:
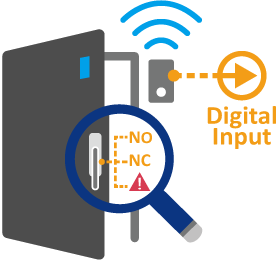
- Digital Input alarms to detect door sensors and locks
The use of door locks and sensors for sensitive equipment. Sensors that are used in conjunction with a lock to the cabinet or chassis can be connected to a managed switch with a digital input (DI). Damage to the door or unauthorized entry to the cabinet will cause the managed switch to send a message to the system administrator or control center.
- Cable loop protection
Access cards and security cameras for high risk areas. Physical access to equipment must be restricted to prevent unauthorized access. This includes not only equipment rooms, but should also take into account exposed cabling. Exposed network cables can be maliciously short-circuited to create a network loop. Cabling that cannot be access protected should have Port Loop Detection enabled on connected switches.
Equipment that is exposed can be enabled with a wide variety of software-based protective measures: - Port Authentication (802.1x Radius)
- Device management interface authentication (TACACS+)
- MAC whitelist
Ethernet port protection: IEEE 802.1x Port Authentication provides an authentication mechanism to devices wishing to attach to a local network. RADIUS is a security protocol that provides centralized authentication for users connecting to a network.

Phase 2 – Detection; identify and record attacks
Network logging and monitoring systems should allow the company to monitor unauthorized data transfers and unauthorized attempts to access the network. The detection system should include detailed alerts and scheduled reports.
Items to be monitored and reported on include:
- Switch login Fail/Success
- 802.1x and TACACS Fail/Success
- Cable loops
- Broadcast storms
- Port abnormally down
Phase 3 – Recovery; Detect damage and bring the system to a safe state
The most important goal of recovery in instances of breaches or attacks is the protection of information assets. Measures taken should be effective in stopping the attack while delivering minimal interruption to IT/OT operations.
Common system actions implemented in response to intrusions and attacks include:
- Setting a wait period of X minutes after successive login fails of Y times.
- Disabling the network for a few minutes when a cable loop is detected.
- Disabling the network for a few minutes when a port storm is detected.
- Set Broadcast/Multicast/Unknown unicast thresholds to block ports when the threshold is reached.
Phase 4 – Remediation; Repair the site and strengthen protection through updates
Firmware updates and patches are critical elements of network security. Both firmware updates and patches are designed to quickly address potential security concerns. It is important to keep an inventory of the devices on your network, including OS types and versions, IP addresses and physical locations. Network utilities such as eVue can simplify the firmware upgrade process on networks with a large number of devices. It can automatically check the firmware version on detected switches, and upgrades can be made through cloud services.

Conclusion
Effective network security requires understanding the potential risks, and implementing both physical and software controls to mitigate them. These four phases of network security are an ongoing process, as existing networks are scaled up and sometimes merged. Choosing the right hardware and software tools is an essential aspect of protecting your company’s data and production lines.
 HANSUN
HANSUN 